DES stands for Data Encryption Standard. It is a symmetric-key block cipher algorithm follows Feistel structure. The data encryption standard is a type of encryption cipher, meaning a way to disguise information from unauthorized parties. DES is a symmetric algorithm, meaning that it uses a single key both to encrypt and decrypt communications and other data.
The DES Algorithm was developed by the IBM team in the 1970s. It was then adopted by the U.S. National Bureau of Standards, now the National Institute of Standards and Technology, or NIST. DES became the approved federal encryption standard in November 1976 and was subsequently reaffirmed as the standard in 1983, 1988, and 1999.
Until the introduction of the Advanced Encryption Standard (AES) in 2001, the Data Encryption Standard (DES) was the most widely used encryption scheme. DES’s dominance came to an end in 2002, when the Advanced Encryption Standard (AES) replaced the DES encryption algorithm as the accepted standard, following a public competition to find a replacement. The DES was officially withdrawn in 2005, although Triple DES (3DES) remains approved for sensitive government information through 2030.
DES
is based on the Feistel block cipher.
It uses 16 rounds of the Feistel
structure, using a different key for each round. DES encrypts data in blocks of size of 64 bits each,
which means 64 bits of plaintext go
as the input to DES, which produces 64
bits of ciphertext. The same algorithm and key are used for encryption and
decryption, with minor differences.
Though, key length is 64-bit, DES has an effective key length
of 56 bits, since 8 of the 64 bits of the key are not used by the encryption
algorithm. Every 8th bit
of the key is discarded to produce a 56-bit key. That is bit positions 8, 16,
24, 32, 40, 48, 56, and 64 are discarded. Thus,
the discarding of every 8th bit of the key produces a 56-bit key from
the original 64-bit key.
Double DES and Triple DES:
As we know the Data encryption standard (DES) uses
56 bit key to encrypt any plain text which can be easily be cracked by using
modern technologies. To prevent this from happening double DES and triple DES
were introduced which are much more secured than the original DES because it
uses 112 and 168 bit keys respectively. They offer much more security than
DES.
Double DES:
Double DES is an encryption
technique which uses two instance of DES on same plain text. In both instances
it uses different keys to encrypt the plain text. Both keys are required at the
time of decryption. The 64 bit plain text goes into first DES instance which
then converted into a 64 bit middle text using the first key and then it goes
to second DES instance which gives 64 bit cipher text by using second key.
Triple DES Algorithm:
Triple DES (TDES
or 3DES) is another encryption algorithm that involves using DES three times to
encrypt a text. While DES encrypts a block of data in 16 rounds, 3DES uses 48
rounds. Although it is a little stronger than DES, 3DES has proven to be
ineffective in securing transmissions. Because 3DES is vulnerable to brute
force attacks, the National Institute of Standards and Technology (NIST) has
officially disallowed the use of 3DES after 2023. It seems the cryptography
world has moved on to AES.
Applications of DES Algorithm:
1. It is used in random number generation
2. It is used whenever a not-very-strong encryption is needed
3. It is used to develop a new form of DES, called
Triple DES (using a 168-bit key formed using three keys)
DES Modes of Operation:
Experts using DES have five different modes of operation to choose from.
- Electronic Codebook (ECB): Each 64-bit block is encrypted and decrypted independently
- Cipher Block Chaining (CBC): Each 64-bit block depends on the previous one and uses an Initialization Vector (IV)
- Cipher Feedback (CFB): The preceding ciphertext becomes the input for the encryption algorithm, producing pseudorandom output, which in turn is XORed with plaintext, building the next ciphertext unit
- Output Feedback (OFB): Much like CFB, except that the encryption algorithm input is the output from the preceding DES
- Counter (CTR): Each plaintext block is XORed with an encrypted counter. The counter is then incremented for each subsequent block
Difference between DES
and AES algorithms:
AES and DES are both examples of symmetric block ciphers but have certain dissimilarities.
DES
|
AES
|
DES stands for Data Encryption Standard
|
AES stands for Advanced Encryption Standard
|
Used to encrypt plain text of 64-bit
|
Used to encrypt plain text of 128-bit
|
The key length is 56-bits.
|
The key length can be 128-bits, 192-bits,
and 256-bits.
|
Bit-Oriented.
|
Byte-Oriented.
|
Less secure than AES
|
More secure than DES
|
It can be broken by brute force attacks
|
There are no known attacks for AES.
|
It is based on Feistel network
|
It is based on permutation and substitution network
|
There are 16 identical rounds of operations.
|
Number of rounds depends on key
length: 10(128-bits), 12(192-bits), or 14(256-bits)
|
DES was designed by IBM.
|
AES was designed by Vincent Rijmen
and Joan Daemen.
|
How does DES work?
DES uses the same key to
encrypt and decrypt a message. Some key features affecting how DES works
include the following:
Block Cipher: The Data
Encryption Standard is a block cipher, meaning a cryptographic key and
algorithm are applied to a block of data simultaneously rather than one bit at
a time. To encrypt a plaintext message, DES groups it into 64-bit
blocks. Each block is enciphered using the secret key into a 64-bit ciphertext
by means of permutation and substitution.
Several
rounds of encryption: The DES
process involves encrypting 16 times. It can run in four different modes,
encrypting blocks individually or making each cipher block dependent on all the
previous blocks. Decryption is simply the inverse of encryption, following the
same steps but reversing the order in which the keys are applied.
64-bit
key: DES uses a 64-bit
key, but because eight of those bits are used for parity checks, the effective
key length is only 56 bits. The encryption algorithm generates 16 different
48-bit subkeys, one for each of the 16 encryption rounds. Subkeys are generated
by selecting and permuting parts of the key as defined by the DES algorithm.
Substitution
and permutation: The algorithm
defines sequences of substitution and permutation that the ciphertext undergoes
during the encryption process.
DES Encryption:
As with any
encryption scheme, there are two inputs to the encryption function: the
plaintext to be encrypted and the key. In this case, plaintext must be 64 bits
in length and the key is 64 bits in length.
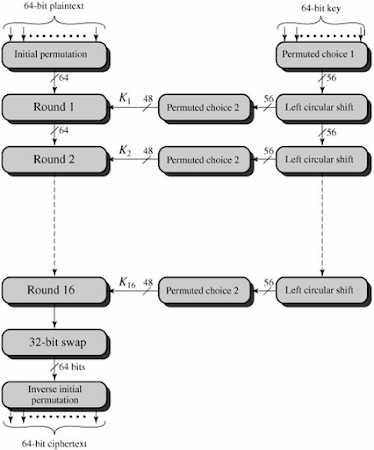
The overall
scheme for DES encryption is illustrated in figure below:
Looking at the left hand side of the figure, we can see that the processing of the plaintext proceeds in three phases. First, the 64 bit plaintext passes through an initial permutation (IP) that rearranges the bits to produce the permuted input.
This
is followed by a phase consisting of 16 rounds of the same function, which
involves both permutation and substitution functions. The output of the last
(16) round consists of 64 bits. The left and right halves of the output are
swapped to produce the preoutput. Finally, the preoutput is passed through an
inverse initial permutation (IP-1) to produce the 64-bit ciphertext.
The right hand side of the figure shows the
way, how the key is initially passed through a permutation function. Then for
each of the 16 rounds, a subkey (Ki) is produced by the combination of a left
circular shift and a permutation. The permutation function is the same for each
round, but a different subkey is produced because of the repeated shifts of the
key bits.
DES
Decryption:
As with any Feistel cipher, decryption uses
the same algorithm as encryption, except that the application of the subkeys is
reversed. Additionally, the initial and final permutations are reversed.
Round Function:
The DES function applies a 48-bit
key to the rightmost 32 bits to produce a 32-bit output as a right.
This function follows some steps,
- Expansion Permutation box
- XOR with the key of 48 bit.
- Substitution Box
- Permutation box.
Expansion Permutation box:
Here,
right half input is 32 bit and the key is 48 bit. We first need to expand right
half input to 48 bits. So, we have to expand the character as we take the 4 bit
of eight block characters. In this, we simply convert the 4 bit of each
character into 6 bit.
So,
we have to expand the 4 bit as in the starting put the bit which presents at
the last character of the bit and in the end put second character first bit.
XOR:
After
the expansion permutation, DES does XOR operation on the expanded right half of
48 bit and the key of 48 bit. The output 48 bit is sent to the S-Boxes.
S-Boxes:
DES
uses 8 S-boxes, each with 6-bit input and a 4-bit output.
The 48
bit data is divided into eight, 6-bit sections and each section is given into
one box. The output of each box is a 4-bit chunk. All eight S-boxes output is
then combined into a 32-bit data. The substitution in each box follows a
predetermined rule based on a 4-row and 16-column table. The combination of
bits 1 and 6 0f the input defines one of the four rows and the combination of
bits 2,3,4 and 5 defines one of the sixteen
columns as shown in figure.
Permutation Box:
The last operation in the DES round function is a permutation with a 32-bit input and a 32-bit output. The input/output relationship for this operation is shown in table below:
Steps for Generating Keys:
There are 16 rounds of
encryption in the algorithm, and a different key is used for each round. How keys are generated is listed below.
DES uses a 64-bit key, but
because of eight of those bits are used for parity checks, the effective key
length is only 56 bits. The encryption algorithm generates 16 different 48-bit
subkeys, one for each of the 16 rounds.
Initially the key consists of 64
bits. The key (64 bit) go as a input to PC-1 (permuted choice-1) and we get
output as 56 bits. Every 8th bit of the key (64 bit) is discarded.
That is bit positions 8,16,24,32,40,48,56 and 64 are discarded.
Thus the discarding of every 8th
bit of the key produces 56-bit key from the original 64-bit key. The output of
PC-1 is 56-bits.
After the permutation, the key
(56 bit) is dividing into two 28-bit parts, C0 and D0. Now these bits are
shifted with left circular shift in each round.
In round 1, 2, 9 and 16, one
bit is shifted i.e., rotated left by 1-bit. In other round it is shifted by
2-bits left circular.
After shifting we get C1, D1
which goes as input to PC-2. C1 and D1 are combined to form 56-bits again. Inside
PC-2, 56-bit bit key is converted to 48-bit key using a predefined table. 56-bits
are rearranged, permuted and 48-bits are selected. Thus we get our first key
for round-1.
Why is DES unsafe?
For any cipher, the most basic method of attack is brute force, which involves trying each key until you find the right one. The length of the key determines the number of possible keys -- and hence the feasibility -- of this type of attack.
The effective DES key length of
56 bits would require a maximum of 256 attempts
to find the correct key. This is not enough to protect data with DES against
brute-force attempts with modern computers.
Few messages encrypted using DES before it was replaced by
AES were likely subjected to this kind of code-breaking effort. Nevertheless,
many security experts felt the 56-bit key length was inadequate even before DES
was adopted as a standard. There have always been suspicions that interference from the National
Security Agency weakened
the original algorithm.
Today, reliance on DES for data confidentiality is a serious
security design error in any computer system and should be avoided. There are
much more secure algorithms available, such as AES. Much like a cheap suitcase
lock, DES will keep the contents safe from honest people, but it won't stop a
determined thief.










0 Comments
if you have any doubts plz let me know...