Network Security:
Network
security is an important field that is increasingly gaining attention as the
internet expands. The field of network security consists of measures to detect,
prevent and correct security violations that involve the transmission of information.
Computer data often travels from one computer to another, leaving the safety of
its protected physical surroundings. Once the data is out of hand, people with
bad intention could modify or forge your data, either for amusement or for
their own benefit.
In simple terms, network security is
securing the network. Network security protects your network and data
from breaches, intrusions and other threats. It is the process of taking preventative
measures to protect the underlying networking infrastructure from unauthorized
access, misuse, malfunction, modification, destruction or improper disclosure. Implementing
these measures allows computers, users
and programs to perform their permitted critical functions within a secure environment.
Network security is the operation of protecting data,
applications, devices, and systems that are connected to the network. Different
policies and practices adopted to prevent any unauthorized access or misuse of
computer networks and related resources are called network security. Also, it
monitors the modifications made or the delay in the network used.
It is a set of rules and configurations designed to protect
the integrity, confidentiality and accessibility of computer networks and data
using both software and hardware technologies.
Network
security entails protecting
the usability, reliability, integrity, and safety of network and data.
Effective network security defeats a variety of threats from entering or
spreading on a network. The primary goal of network security are:
Confidentiality, Integrity, and Availability.
Network
security is a category of practices and technologies that keep internal
networks protected from attacks and data breaches. It
encompasses access control, cyber attack prevention, malware detection,
and other security measures. An effective network security plan is developed
with the understanding of security issues, potential attackers, needed level of
security, and factors that make a network vulnerable to attack
Network
security does not only concern the security in the computers at each end of the
communication chain. When transmitting data the communication channel should
not be vulnerable to attack. A possible hacker could target the communication
channel, obtain the data, decrypt it and re‐insert a false message.
Securing the network is just as important as securing the computers and
encrypting the message.
Network security is an organization’s strategy that
guarantees the security of its assets, including all network traffic. It
includes both software and hardware technologies. Access to the network is
managed by adequate network security, which targets many threats and then
arrests them from spreading or entering the network.
Role
of Network Security:
The Role of network security includes the following:
- Prevent unauthorized access to assets and data.
- Protect network data, infrastructure, and all traffic from external threats.
- Stop threats from spreading through the system.
- Enable secure data sharing between systems and employees.
- Grant users adequate access to resources.
- Detect and respond to suspicious user behavior and software anomalies.
- Scanning the network for viruses, Trojans, and other malicious software.
- Creating new rules to protect against malware infections.
- Monitoring the network for suspicious activity such as suspicious email attachments or suspicious website behaviour.
Need for Network Security:
The
use of the Internet has increased drastically, as we are moving even our
day-to-day activities towards complete digitalization. Due to the increase in
the use of the Internet, hackers and attackers also become more active and our
networking system tends to have a higher number of virus attacks.
Basically,
the need for network security is to perform two tasks mainly, the first is to
secure the information from any unauthorized access and the second is to
provide the security to the data stored on PC or laptops not only for an
individual network but also on the shared or public domain networks.
Network security is one of the most
important aspects to consider when working over the internet. A stable and efficient
network security system is essential to protecting client data. A good
network security system helps business reduce the risk of falling victim of
data theft and sabotage. Network security helps protect your workstations from
harmful spyware. It also
ensures that shared data is kept secure.
Network
security ultimately protects the recognition of your organization. With hackers
increasing and becoming smarter day by day, the need to utilize network security tools becomes
more and more important.
Benefits of Network Security/ Importance of Network security:
Unless it’s properly secured, any network is vulnerable to malicious use and accidental damage. Hackers, disgruntled employees, or poor security practices within the organization can leave private data exposed, including trade secrets and customers’ private details.
The majority of common attacks against networks are designed to gain access to information, by spying on the communications and data of users, rather than to damage the network itself. But attackers can do more than steal data. They may be able to damage users’ devices or manipulate systems to gain physical access to facilities. This leaves the organization’s property and members at risk of harm.
Competent network security
procedures keep data secure and block vulnerable systems from outside
interference. This allows the network’s users to remain safe and focus on
achieving the organization’s goals. More than that, it means that clients and
partners can also interact with the organization confidently.
Network security tools and devices exist to help your
organization protect not only its sensitive information but also its overall
performance, reputation and even its ability to stay in business. Continued
operational ability and an intact reputation are two key benefits of effective
network security.
Secure and reliable networks protect not just organizational
interests and operations, but also any client or customer who exchanges
information with the organization, in addition to the general public. A well
designed network security solution reduces overhead expenses and safeguards
organizations from costly losses that occur from a data breach or other
security incident.
Here’s why both
businesses and households should consider the security of their networks
seriously:
To protect the computers in the network: Computers and other devices connected to unsecured networks are highly vulnerable to external threats such as malware, ransomware and spyware attacks. A single attack can bring down the entire computer system of an organization and compromise your personal information. By assuring the security of the network – typically with the assistance of a network security specialist – you can stay away from such expensive threats.
To prevent identity theft: No matter whether you are an organization or an individual, your identity is valuable. If you log into an unsecured network, your identity can become visible to third-parties. To avoid such a situation, you should secure your network. Such an approach becomes mandatory if you are a business that deals with client information.
To protect shared data: When it comes to a business, special precautions should be taken to protect shared data. And, network security is one of the best ways to do so. Network security can be applied with different restrictions on different computers depending on the types of files they handle.
To stabilize the network connection: In an unrestricted,
unprotected network, network activity can become too heavy. Intense traffic can
lead to an unstable computer network. Eventually, the entire network will
become vulnerable to various external attacks.
Goals of Network security or Objectives of Network Security:
Network security is the process through
which a network is secured against internal and external threats of various
forms. Network
security is not only concerned about the security of the computers at each end
of the communication chain; however, it aims to ensure that the entire network
is secure.
Network security necessitates
protecting the usability, stability, honesty, and security of network and also
data. It aims to guarantee that the whole system is secure.
Network
security entails protecting the usability, reliability, integrity, and safety
of network and data. Effective network security defeats a variety of threats
from entering or spreading on a network.
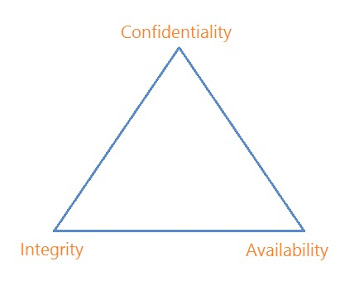
The primary goals
of network security are Confidentiality,
Integrity, and Availability. These three pillars of Network Security are
often represented as CIA triad (CIA triangle).
Confidentiality: The first goal of Network Security is "Confidentiality". Confidentiality means preserving
authorized restrictions on information access and disclosure. Making sure
people cannot attain the information they should not (keeping secrets).
It is the protection of data from unauthorized disclosure. Confidentiality
can be defined as permitting approved users for
accessing all sensitive as well as protected information. The
confidentiality aspect of network security involves keeping the data private.
The
function of confidentiality is to protect precious business data from
unauthorized persons. Confidentiality part of network security makes sure that
the data is available only to the intended and authorized persons. A loss of
confidentiality is the unauthorized disclosure of information.
Confidentiality
ensures that the information is not read by anyone for whom it was unintended
and is read only by authorized parties. All information during the transaction
has the request of being kept confidential. Information should not be
accessible to unauthorized person. It should not be intercepted during
transmission.
Integrity: The second goal of Network Security is "Integrity". Integrity
means guarding against improper information modification or destruction. Making
sure people cannot change the information they should not (protecting data). Integrity
aims at maintaining and assuring the accuracy and consistency of data.
The
function of integrity is to make sure that the data is accurate and reliable and is not changed by unauthorized persons or hackers. The
data received by the recipient must be exactly same as the data sent from the
sender, without change in even single bit of data. A loss of integrity is the
unauthorized modification or destruction of information.
Integrity
ensures that the information wasn’t altered in storage or transit between
sender and intended receiver. Information should not be altered during its
transmission over the network. The assurance
that data received are exactly as sent by an authorized entity (i.e., contain
no modification, insertion, deletion or replay). Integration prevents the
unauthorized modification of data.
Availability: The third goal of network security is "Availability". As
the name suggests, availability specifies whether the data or resource is
available when required or requested by the client. Making sure people
cannot stop the computer from doing its job.
Availability
means ensuring timely and reliable access to and use of information. The
function of availability in Network Security is to make sure that the data,
network resources or network services are continuously available to the
legitimate users, whenever they require it. A loss of availability is the
disruption of access to or use of information or an information system.
Although the use of CIA triad to define security objectives is well established, some in the security field feel that additional concepts are needed to present a complete picture. Two of the most commonly mentioned are as follows:
Authenticity: Authenticity
is the property of being genuine and being able to be verified and trusted;
confidence in the validity of a transmission, a message, or message originator.
Authenticity ensures that the sender and receiver can confirm each others
identity and the origin/destination of the information.
Authenticity is assurance that a message, transaction, or
other exchange of information is from the source it claims to be from.
Authenticity involves proof of identity. We can verify authenticity through
authentication.
Authentication can be defined as the process of ensuring and
confirming that the identity of the user is genuine and legitimate. Authentication prevents impersonation and
requires users to confirm their identities before being allowed access to
systems and resources. This includes user names, passwords, emails,
biometrics, and others.
Accountability: Accountability is the principle that an individual is entrusted to
safeguard and control equipment, keying material, and information and is
answerable to proper authority for the loss or misuse of that equipment or
information.
It is the security goal that generates the requirement for
actions of an entity to be traced uniquely to that entity. This supports
non-repudiation, deterrence, fault isolation, intrusion detection and
prevention, and after-action recovery and legal action. Because truly secure
systems are not yet an achievable goal, we must be able to trace a security
breach to a responsible party. Systems must keep records of their activities to
permit later forensic analysis to trace security breaches or to aid in
transaction disputes.
OSI Security
Architecture:
OSI (Open System Interconnection) Security Architecture defines the
well-planned standard architecture for security features in computer
networking.
It
is a recommendation of the International Telecommunication Union which defines
a systematic approach to define security requirements for a certain
organization, as well as approaches to meet the aforementioned requirements.
The
OSI security architecture provides a general description of security services
and mechanisms, as well as a description of security attacks.
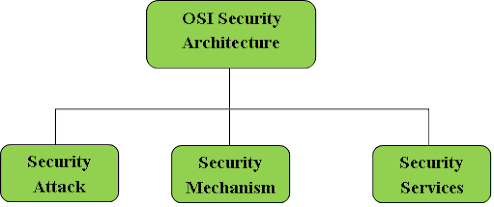
Classification of OSI
Security Architecture:
OSI Security Architecture is categorized
into three broad categories:
Security Attack: Any action
that compromises the security of information owned by an organization.
Security Mechanism: A mechanism that is
designed to detect, prevent, or recover from a security attack.
Security Service:
A processing or communication service that enhances the security
of the data processing systems and the information transfers of an
organization.
Security Attacks:
A security attack means any action
that puts the data or overall security of the system at risk. An attack might
be successful or unsuccessful. In case of a successful attack, the attacker can
complete his/her motive of breaking the security of the system in any way
he/she wants to. In case of an unsuccessful attack, the system remains secured
and no harm to the security is done.
A useful
means of classifying security attacks, used both in X.800 and RFC 4949, is in
terms of passive attacks and active attacks.
Passive Attacks:
In passive network attacks,
attackers gain unauthorized access to a network and can monitor or steal
sensitive information, without making any alterations.
In passive attack a system is monitored and sometimes scanned
for open ports and vulnerabilities. The purpose of a passive attack is to gain
information about the system being targeted; it does not involve any direct
action on the target. The attacker does not modify or corrupt the data. No changes are
made to the data.
A Passive attack attempts to learn or make use of information from the system but does not affect system resources. There are 2 types of passive attacks.
- Release
of message content
- Traffic
analysis
Release of message content: Telephonic
conversation, an electronic mail message, or a transferred file may contain
sensitive or confidential information. We would like to prevent an opponent
from learning the contents of these transmissions.
Traffic
Analysis: As
the name suggests, this attack focuses on the amount or volume of data sent
between the sender and the receiver. The attacker can predict a lot of
information about the sender and the receiver by knowing the amount of data
sent. For example, if a lot of data is being sent from the sender to the receiver,
it is assumed as there is an emergency, or a task is happening on an urgent
basis. If less data is shared between the sender and the receiver, it is
assumed that there is a lack of communication and so on.
Suppose that we had a way of masking (encryption)
information, so that the attacker even if captured the message could not
extract any information from the message.
The opponent could determine the location and identity of communicating host
and could observe the frequency and length of messages being exchanged. This
information might be useful in guessing the nature of the communication that
was taking place.
Active
Attacks:
In active attacks attackers not only gain
unauthorized access but also modify data either deleting, encrypting or
otherwise harming it. Attackers gain
unauthorized access to the network and then modify data (say, via encryption)
to compromise it and affect its usability and value.
An Active attack attempts to alter system resources or affect their operations. Active attacks involve some modification of the data stream or the creation of false statements.
Active attacks are subdivided into four categories:
- Masquerade
- Replay
- Modification of messages
- Denial of Service
Masquerade: A masquerade attack takes
place when one entity pretends to be a different entity. In this attack too, the attacker acts to be an
authorized user. A Masquerade attack involves one of the other forms of
active attacks. If an authorization procedure isn’t always absolutely
protected, it is able to grow to be extraordinarily liable to a masquerade
assault. Masquerade assaults may be performed using the stolen passwords and
logins, with the aid of using finding gaps in programs, or with the aid of
using locating a manner across the authentication process.
Modification of messages: It
means that some portion of a message is altered or that message is delayed or
reordered to produce an unauthorized effect. Modification is an attack on the
integrity of the original data. It basically means that unauthorized parties
not only gain access to data but also spoof the data by triggering
denial-of-service attacks, such as altering transmitted data packets or
flooding the network with fake data.
Replay: It involves the passive capture of a message and its subsequent transmission to produce an authorized effect. In this attack, the basic aim of the attacker is to save a copy of the data originally present on that particular network and later on use this data for personal uses. Once the data is corrupted or leaked it is insecure and unsafe for the users.
Denial of Service: The denial-of-service (DoS) attack is an attack in which a system is attacked by a lot of requests to the system at one time that it is not able to handle. The attacker sends multiple requests to the server at the same time and the server is not able to handle such requests. However, this attack is easily identifiable as these loads of requests come from a single sender (the attacker) and it is easy to identify the source of the attack.
It prevents the
normal use of communication facilities. This attack may have a specific target.
For example, an entity may suppress all messages directed to a particular
destination. Another form of service denial is the disruption of an entire
network either by disabling the network or by overloading it with messages so
as to degrade performance.
Denial of
service is a method used by hackers to send a large number of automated
requests to a website. To the website server, these requests seem to originate
from genuine visitors. So the website server attempts to respond to the
requests. But the sheer volume overwhelms the server. Although a DoS attack
does not usually result in the theft of information or other security loss, it
can cost the target person or company a great deal of time and money.
Typically, the loss of service is the inability of a particular network
service, such as e-mail, to be available or the temporary loss of all network
connectivity and services. A denial of service attack can also destroy programming
and files in affected computer systems.
Security Services:
X.800
defines a security service as a service that is provided by a protocol
layer of communicating open systems and that ensures adequate security of the
systems of data transfers.
RFC 4949
defines a security service as a processing or communication service that
is provided by a system to give a specific kind of protection to system
resources; security services implement security policies and are implemented by
security mechanism.
Security service is a processing or communication service that
enhances the security of the data processing systems and the information
transfers of an organization. The services are intended to counter security
attacks, and they make use of one or more security mechanisms to provide the
service. These are the services that are used for maintaining security. These
security services can be implemented in various layers of the OSI model.
X.800 divides security
services into 5 categories and 14
specific services.
Authentication:
The
authentication service is concerned with assuring that a communication is
authentic. Authentication is the assurance that the communicating entity is the
one that it claims to be.
In
the case of a single message, such as a warning or alarm signal, the function
of the authentication service is to assure the recipient that the message is
from the source that it claims to be from.
In
the case of an ongoing interaction, such as the connection of a terminal to a
host, two aspects are involved. First, at the time of connection initiation,
the service assures that the two entities are authentic, that is, that each is
the entity that it claims to be. Second, the service must assure that the
connection is not interfered with in such a way that a third party can
masquerade as one of the two legitimate parties for the purposes of
unauthorized transmission or reception.
Two specific
authentication services are defined in X.800:
Peer Entity
Authentication: Provides for the corroboration of the identity of a peer
entity in an association. It attempts to
provide confidence that an entity is not performing either a masquerade or an
unauthorized replay of a previous connection.
Peer
entity authentication used in association with a logical connection to provide
confidence in the identity of the entities connected. It is the process of verifying that a peer entity in an association is
as claimed.
Peer
entity authentication means verifying the identity of one entity by another.
Data Origin
Authentication: Provides for the corroboration of the source of a data
unit. In a connectionless transfer, provides assurance that the
source of received data is as claimed.
Data
origin authentication means verifying the origin of received data. It does not
provide protection against the duplication or modification of data units. This
type of service supports applications like electronic mail, where there are no
prior interactions between the communicating entities.
Access Control:
The prevention of unauthorized use of a resource i.e., this
service controls who can have access to a resource, under what conditions
access can occur, and what those accessing the resource are allowed to do.
In the context of network security, access
control is the ability to limit and control the access to host systems and
applications via communications links.
In
an organization, various levels of employees have various levels of access to
the system. For example, in a company, a software engineer has limited access
to the system as compared to the product manager and the product manager has
limited access as compared to the CTO of the company.
Data Confidentiality:
This is one of the three
pillars of the security model CIA (Confidentiality, Integrity, and
Availability). Confidentiality means that the data shared between a sender and
receiver should be confidential to them only. No third party should be able to
read the data. Confidentiality is the protection of data from unauthorized
disclosure. When preventing
disclosure of information to unauthorized parties is needed, the property of
confidentiality is required.
To
provide confidentiality, the cryptographic algorithm and mode of operation
needs to be designed and implemented in such a way that an unauthorized party
will be unable to determine the keys that have been associated with the
encryption or have the ability to derive the information without using the
correct keys.
Confidentiality
is the protection of transmitted data from passive attacks. With respect to the
content of a data transmission, several levels of protection can be identified.
The broadest service protects all user data transmitted between two users over
a period of time. For example, when a TCP connection is set up between two
systems, this broad protection prevents the release of any user data
transmitted over the TCP connection. Narrower forms of this service can also be
defined, including the protection of a single message or even specific fields
within a message. The other aspect of confidentiality is the protection of traffic
flow from analysis. This requires that an attacker not be able to observe the
source and destination, frequency, length, or other characteristics of the
traffic on a communications facility.
Connection Confidentiality: The protection of all user data on a connection.
Connectionless Confidentiality: The protection of all user data in a single data
block
Selective-Field Confidentiality: The confidentiality of selected fields within the
user Data on a connection or in a single data block.
Traffic Flow Confidentiality: The protection of the information that might be derived
from observation of traffic flows.
Data
Integrity:
This
is the second pillar of the CIA. Here, integrity means that no third party
should be able to modify the data shared between the sender and the receiver.
Data
integrity is the assurance that data received are exactly as sent by an
authorized entity (i.e., contain no modification, insertion, deletion, or
replay).
As with confidentiality, integrity can apply to a stream of
messages, a single message, or selected fields within a message. Again, the
most useful and straightforward approach is total stream protection.
A connection-oriented integrity service, one
that deals with a stream of messages, assures that messages are received as
sent with no duplication, insertion, modification, reordering, or replays. The
destruction of data is also covered under this service. Thus, the
connection-oriented integrity service addresses both message stream
modification and denial of service. On the other hand, a connectionless
integrity service, one that deals with individual messages without regard to
any larger context, generally provides protection against message modification
only. We can make a distinction between service with and without recovery.
Because the integrity service relates to active
attacks, we are concerned with detection rather than prevention. If a violation
of integrity is detected, then the service may simply report this violation,
and some other portion of software or human intervention is required to recover
from the violation. Alternatively, there are mechanisms available to recover
from the loss of integrity of data, as we will review subsequently. The
incorporation of automated recovery mechanisms is, in general, the more
attractive alternative
Connection Integrity
with Recovery:
Provides for the integrity of all user data on a connection and detects any
modification, insertion, deletion, or replay of any data within an entire data
sequence, with recovery attempted.
Connection
Integrity without Recovery: As above, but provides only detection without
recovery.
Selective-Field
Connection Integrity:
Provides for the integrity of selected fields within the user data of a data
block transferred over a connection and takes the form of determination of
whether the selected fields have been modified, inserted, deleted, or replayed.
Connectionless
Integrity:
Provides for the integrity of a single connectionless data block and may take
the form of detection of data modification. Additionally, a limited form of
replay detection may be provided.
Selective-Field
Connectionless Integrity: Provides for the integrity of selected fields within a
single connectionless data block; takes the form of determination of whether
the selected fields have been modified.
Non-
Repudiation:
Non-repudiation
provides protection against denial by one of the entities involved in a
communication of having participated in all or part of the communication. It
prevents either sender or receiver from denying a transmitted message. Thus,
when a message is sent, the receiver can prove that the alleged sender.
Non-Repudiation
ensures that the sender of the information cannot deny at a later stage his or her
intentions in the creation or transmission of the information.
Non-repudiation, Origin: Proof that the message
was sent by the specified party.
Non-repudiation,
Destination:
Proof that the message was received by the specified party.
Security Mechanisms:
Security
mechanisms are technical tools and techniques
that are used to implement security services. The security mechanisms provide a way of
preventing, protecting and detecting attacks.
Security mechanism is designed to detect,
prevent, or recover from a security attack. The
mechanisms that help in setting up the security services in different layers of
the OSI model and that help in identifying any attack or data breach are called
security mechanisms.
Security
mechanisms are the specific means of
implementing one or more security services. The mechanisms are divided into
those that are implemented in a specific protocol layer and those that are not
specific to any particular protocol layer or security service.
The security mechanisms defined in X.800 are explained below:
Specific Security
Mechanisms:
Specific
security mechanisms may be incorporated into the appropriate protocol layer in
order to provide some of the security services.
The
OSI security architecture enumerates eight
specific security mechanisms.
Encipherment:
This security mechanism deals with hiding
and covering of data which helps data to become confidential. It is achieved by
applying mathematical calculations or algorithms which reconstruct information
into not readable form.
One
of the most popular security mechanisms is encryption. The message/data sent
from the sender to the receiver is usually encrypted to some format that even
if the message is stolen, cannot be decrypted easily by the attacker. Some of
the popular encryption algorithms are AES, RSA, Triple DES, etc.
Digital Signature: A digital signature is
an analytical approach which validates the authenticity and integrity of a message,
application or digital records. It allows us to test the author name, date and
time of signatures, and verify the message text.
The digital signature supports far more basic
security and designed to solve the problem of tampering and impersonation (deliberately
copy another person's features) in electronic connection.
Data or cryptographic transformation of an
information unit is additional to the data, therefore that the recipient of the
information unit is converted of the source and integrity of the information
unit and this can also serve to secure the data against forgery (such as by the
recipient).
Access Control: Access control is an
information security process that enables organizations to manage who is
authorized to access corporate data and resources.
Secure access control need policies that check
users are who they claim to be and support proper control access levels are
allowed to users. There are several structure are available that accomplish
access rights to resources.
This
mechanism is used to stop unattended access to data which you are sending. It
can be achieved by various techniques such as applying passwords, using
firewall, or just by adding PIN to data.
Data Integrity: Integrity can use to a
flow of messages, an individual message, or selected areas inside a message. In
data integrity, it is a connection-oriented integrity service, it can handle
with a flow of messages, and assure that messages are received as sent with no
duplication, insertion, modification, reordering, or replays.
Authentication Exchange: A mechanism intended to
ensure the identity of an entity by means of information exchange. Such a
mechanism consists of an exchange of messages between a pair of entities.
This security mechanism deals with
identity to be known in communication. This is achieved at the TCP/IP layer
where two-way handshaking mechanism is used to ensure data is sent or not.
Traffic
Padding: Traffic padding mechanisms are used to
protect against traffic analysis attacks.
The
sender and receiver send the data to each other. Now, sometimes there is a gap
between the sender and receiver. This means that for some time when the sender
and receiver are not sharing the data, the attacker can act as if it is the
sender and send some data to the receiver to attack it. So, this can be avoided
if the gap (empty time) between the sender and the receiver is not known to the
attacker. For this, during the gap duration, the sender keeps on sending some
dummy data to the receiver and the receiver knows that this is the dummy data
by using some identification. Hence, no gap is created between the sender and
the receiver and the attacker cannot attack the system.
Routing
Control: Routing control enables selection of particular physically
secure routes for certain data and allows routing changes, especially when a breach
of security is suspected.
The
messages that a sender sends to a receiver travel different routes, however, in
some cases, the sender and receiver might communicate mostly via the same
route. In this case, the attacker tracks this route and can make changes to the
data or take advantage of this. So, routing should be controlled in such a way
that mostly, a different route is selected between the sender and the receiver
to deliver the message.
Notarization: Notarization is the
usage of a trusted third party to assure certain properties of a data exchange.
This security mechanism involves use of
trusted third party in communication. It acts as mediator between sender and
receiver so that if any chance of conflict is reduced. This mediator keeps
record of requests made by sender to receiver for later denied.
Notarization mechanisms can be used to
assure certain properties of the data communicated between two or more
entities, such as its integrity, origin, time, or destination. The assurance is
provided by a trusted third party (TTP) in a testifiable manner.
Pervasive Security
Mechanisms:
Pervasive
security mechanisms are not specific to any particular security service. The
OSI security architecture enumerates five
pervasive security mechanisms.
Trusted Functionality: Trusted functionality is the process which is perceived
to be correct with respect to some criteria (e.g., as established by a security
policy).
The
general concept of trusted
functionality can be used to either extend the scope or to
establish the effectiveness of other security mechanisms. Any functionality
that directly provides, or provides access to, security mechanisms should be
trustworthy.
Security Label: This is an approach of
marking bound to a resource (which may be a data unit) that names or designates
the security attributes of that resource.
System resources may
have security labels associated
with them, for example, to indicate sensitivity levels. It is often necessary
to convey the appropriate security label with data in transit. A security label
may be additional data associated with the data transferred or may be implicit
(e.g., implied by the use of a specific key to encipher data or implied by the
context of the data such as the source address or route).
Event Detection: Detection of
security-relevant events including forgery, denial of sending or receiving of
information, modification of information etc.
Security Audit Trail: A security audit refers to an
independent review and examination of system records and activities to test for
adequacy of system controls, to ensure compliance with established policy and
operational procedures, to detect breaches in security, and to recommend any
indicated changes in control, policy, and procedures. Consequently, a security audit trail refers to
data collected and potentially used to facilitate a security audit.
It supports a valuable security mechanism, as
possibly they allow detection and analysis of breaches of security by allowing
a subsequent security audit. A security audit is an independent report and
investigation of system data and events in order to test for sufficiency of
system controls, to provide compliance with established policy and operational
processes, to help in loss assessment and to approve some indicated changes in
controls, policy and processes.
Security Recovery: Security
recovery deals with requests from mechanisms such as event handling
and management functions, and takes recovery actions as the result of applying
a set of rules.
Relationship between Security
Services and Mechanisms:
Security services and mechanisms are closely related because a mechanism or combinations of mechanisms are used to provide a service.
Security mechanisms are technical tools and
techniques that are used to implement security services. A mechanism might
operate by itself, or with others, to provide a particular service.
|
Service |
Mechanism |
|||||||
|
|
Encipherment
(Encryption) |
Digital
signature |
Access
control |
Data
integrity |
Authentication
exchange |
Traffic
padding |
Routing
Control |
Notarization |
|
Peer entity authentication |
Y |
Y |
|
|
Y |
|
|
|
|
Data origin authentication |
Y |
Y |
|
|
|
|
|
|
|
Access control |
|
|
Y |
|
|
|
|
|
|
Confidentiality |
Y |
|
|
|
|
|
Y |
|
|
Traffic flow confidentiality |
Y |
|
|
|
|
Y |
Y |
|
|
Data integrity |
Y |
Y |
|
Y |
|
|
|
|
|
Nonrepudiation |
|
Y |
|
Y |
|
|
|
Y |
|
Availability |
|
|
|
Y |
Y |
|
|
|





0 Comments
if you have any doubts plz let me know...